This is the second part of our series "Digitalisation 2021". In the other articles, learn about digitalisation in the fields of sales, marketing, logistics, finance, procurement, manufacturing and controlling. The focus of this article is on digitalisation in IT security.
Do you still remember? In 2015, the German parliament was successfully attacked by hackers. In 2017, the ransomware WannaCry attacked and paralyzed more than 100,000 computers in 150 countries. Car factories could no longer produce, and computers and MRI scanners in hospitals stood still. But the world's most threatening cyberattack happened in 2010, when the Stuxnet computer worm was deployed and manipulated the controls and motors of Siemens industrial equipment. This was a targeted attack on uranium centrifuges at enrichment plants and on Iran's nuclear program, which has been set back for years as a result.
That all sounds far away? According to a Bitkom survey, three out of four companies fell victim to industrial espionage, data theft and sabotage from 2017 to 2019. The main target group? Organizations with up to 99 employees, which often lack the resources to protect themselves against these attacks.
The Foundation of the Digital Transformation
In the course of the digital transformation, computers are being assigned more tasks and linked to each other. Consequently, there is a greater potential for attacks, and the consequences of targeted cyberattacks are far more devastating. Currently (2021), every second out of three companies is already under attack. The BSI (German Federal Office for Information Security) even talks about cyber security as a competitive advantage in digitization and has published a brochure of the same name on the subject.
Prevention is no more sufficient today. Nowadays, attacks must be detected quickly in order to limit the damage and eliminate the causes. At the same time, security enables and accelerates digitization and digital growth strategies.
In the following, you will read about the things you should pay attention to in order to create this solid foundation.
The challenges of digitalization for cybersecurity
As Covid-19 accelerates digitization and the acceptance of the home office, the physical boundaries of any business are visibly disappearing. This poses a further challenge to IT security, which is already strained with the growing interconnectedness of more and more computers, which in turn can perform more and more tasks autonomously.
The following points are critical aspects and popular gateways for attackers.
1. Cloud Security
The cloud has a lot to offer. There is global access around the clock, which is indispensable for teams and projects working at different locations. Or for individual employees at home. Complete infrastructures can be implemented virtually here. The advantages in terms of agility, flexibility and scalability are significant. And when it comes to data backup, you can sit back and relax. But not when it comes to security.
Holistic approach
As with IT security as a whole, cloud security must be viewed holistically. Especially when multi-cloud environments are used, i.e., the use of multiple cloud services and providers.
With DevOps software development (DevOps stands for "development" and "operations" and combines the previously separate areas of development and operations), the DevSecOps approach takes effect here, anchoring security comprehensively in the entire process right from the start.
Cloud configuration
The human source of error - Gartner states that in most cases it is not the cloud provider but the user who fails to configure the cloud, thus exposing trade secrets, intellectual property and sensitive information. Access control as well as access management must be scrupulously observed when configuring the cloud.
APIs
Another popular vulnerability are insecure programming interfaces, called APIs (application programming interface). Interested readers can find the OWASP API Security Top 10 list here, a widely used list of the top ten vulnerabilities in web applications.
System vulnerabilities
Last but not least, the cloud provider itself is also vulnerable to attacks. That is why, in addition to secure applications, regular vulnerability and security checks must also be carried out at the provider.
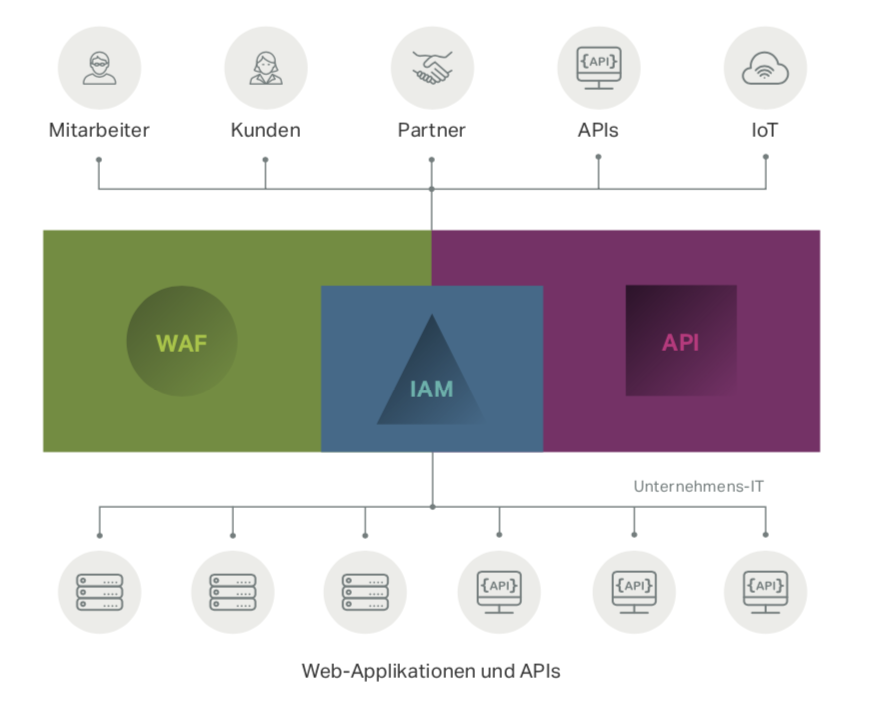
2. Authentication and identity & access management (IAM)
Identity protection is also at the top of the security agenda. The classic combination of user name and password is no longer sufficient for access protection these days. In addition, two-factor authentication should be used, i.e., proof of a user's identity by means of a combination of two different and, in particular, independent components. Examples of this would be the bank card plus pin for ATMs, security token plus access code in buildings, or even user name/password on the PC plus security code from an authentication app on the smartphone.
Identity and access management (IAM) also involves defining and managing the roles and access rights of individual network users. Every employee is given a digital identity that must be maintained, changed and monitored. There should never be one identity that can access everything.
3. Endpoint Security
The so-called endpoint security has many names - endpoint safety, endpoint device safety or endpoint protection. It is about securing endpoints or end-user devices. So, for example, PCs, notebooks, smartphones and tablets. These also provide access to the corporate network and are therefore potential gateways for hackers. As the name suggests, endpoint security protects endpoints from attacks and serves to comply with important data protection and compliance requirements. Organizational measures such as raising awareness or training employees on how to handle endpoints and external data carriers are also part of this.
The Endpoint Security system is a software and platform that analyzes, monitors and protects all network traffic between endpoints and the network. For system administrators, this platform provides a central console with which they can detect attacks or suspicious activity at an early stage. They also have direct access to endpoints if they have been configured appropriately.
Methods such as secure virtualized surfing environments or email gateways to block phishing and fraud attempts against employees (social engineering, see below) help avert cyberattacks.
4. Social engineering - human vulnerability
Let's take a closer look at social engineering. Social engineering is the psychological manipulation of people and is often the start of a cyberattack. The attacker gains information, gets someone to click a link, or even gains access to a supposedly secure IT system. But how is this possible? - Social engineering exploits human traits and emotions such as helpfulness, trust, fear, greed, rage or respect for authority so that the desired action is eventually performed by the victim. "The central feature of attacks using social engineering is deception about the identity and intent of the perpetrator," is the BSI's (German Federal Office for Information Security) statement on the matter.
An endpoint security system is an effective measure against social engineering, as e-mail gateways filter fraudulent e-mails on the one hand, and employees are trained according to security risks on the other.
Sensitization of your employees is essential in any case. This also includes what information they publish in social media, which includes both the professional and private spheres.
The most popular social engineering methods are phishing (mass fraud attempt) and spear phishing (strategic fraud attempt). In both cases, emails are sent that disguise identity and contain an intent on the part of the perpetrator. While phishing emails are usually easy to recognize as such, the spear phishing variant can even deceive very careful and critical employees. Trust may have been built up with an individual employee for weeks in advance of such an email before the attack occurs.
For a quick introduction, watch the video "Email security in 3 seconds" provided by the BSI.
Digitization of IT security
And what about digitization in IT security itself? By its very nature, the IT department is inherently digitized. Nevertheless, there are also innovations here that are driving digitization. When it comes to cybersecurity, the focus is on two areas that are often very closely wired together: Automation and Artificial Intelligence (AI).
In the digitization of IT security, Artificial Intelligence is used to detect anomalies. If something seems suspicious, the designated automation kicks in and acts according to certain rules or the AI's level of knowledge. The security administrator only gets to see the report in the end. As a result, the workload is transferred to the machine, whereas a human would easily be overwhelmed - because the number of attacks continues to grow every day, as does their complexity and sophistication.
IT Security for the Industry 4.0
As we learned in the introduction, attacks on networked Industry 4.0 systems can pose a real threat to human life - as was the case in September 2020 with an accidental hacker attack on a university hospital server in Düsseldorf, whose actual target was the university.
Smart Factory risk
Industry 4.0 with its smart factories and the Internet of Things (IoT) is particularly at risk. On the one hand, this is due to the fact that IdD devices have insufficient or no cyber security. And on the other hand, this is where business processes meet production processes. IT meets OT, IT meets OT, Information Technology meets Operational Technology. OT encompasses the operation of physical processes and the machines used to perform them. Once again, these intersections offer an increased area of attack for intruders and must be fully monitored within the company.
Data security takes on a key role
Again, a holistic strategy is essential and IT as well as OT security is a basic requirement for Industry 4.0. However, experts complain that this issue has still not reached management. While IT security is a matter of course (now also an integral part of modern software development), OT security is a relatively new area. The aggravating factor is that other responsibilities apply to production and those responsible for IT security are simply left out of the loop here. Data security must become a management issue.
Ways towards a Smart Factory
A smart factory requires digital communication across the company. However, business processes are often not available in digital form - on the one hand, this approach is also relatively new for the company, and on the other hand, confidentiality as well as business secrets are at stake. An IT security auditor helps to analyze existing information systems and initiates necessary corrective or improvement measures. Looking at medium-sized businesses, the digitalization of business processes is the first step. In this context, an end-to-end process description that enables seamless automation can be challenging enough. A key position here is occupied by the IT security engineer, who takes on such challenges. The benefits pay off in the long run - in the form of automated processes that can be further optimized, as well as communication with production, sales, employees and customers.

Conclusion
Digitalization has significantly multiplied the complexity and vulnerability of both IT and OT security. There is no simple solution here. Understanding the individual components and systems alone is already demanding, but in combination, the complexity becomes almost unmanageable.
But there are just as many ways to contain the risk of digital transformation. It is essential to take a holistic view of the enterprise and know the entire security risk lifecycle to create a comprehensive concept as well as strategy and implementation. This includes end users and their identities, endpoints, remote access, cloud security, data storage locations, human vulnerability, and employee awareness of IT security.
Security by design in business
"Secure by design" or also "security by design" is a term from software development, which in relation to companies means that IT security forms the basis of every development and the entire digitalization. This lays the foundation for healthy cyber resilience, i.e., the holistic strategy for strengthening a company's resistance to cyber attacks. What is needed here is an open and integrated IT security that can act company-wide to avoid isolated solutions and gaps in the strategy. A CISO in the company automatically brings IT security to the management level.
If this position is lacking, other security experts such as the IT security engineer must be given the necessary authority to implement a holistic strategy and anchor security in the corporate culture.
This is the second part of our series "Digitalization 2021". Learn about the importance of Digital Transformation in Marketing in the next article.
Part 1: Digitalization in sales
.svg)









.jpg)



